The unintentional, fraudulent leakage of data from a company represents a major challenge for the affected companies that goes beyond the immediate handling of the IT security incident. Data leaks, in particular, are multifaceted and complex in their need to be addressed. Furthermore, they can lead to immense financial as well as reputational damage.
In order to keep the corresponding damage as low as possible, it is of enormous importance to clarify such cyber attacks immediately and completely and to bring transparency to the incident. Immediately, questions arise such as:
- Which data has been leaked?
- Are trade secrets, third-party data or personal data affected?
- Am I being blackmailed?
- What are my obligations to data subjects, third parties and supervisory authorities?
- Which persons do I have to involve internally and which processes have to be created?
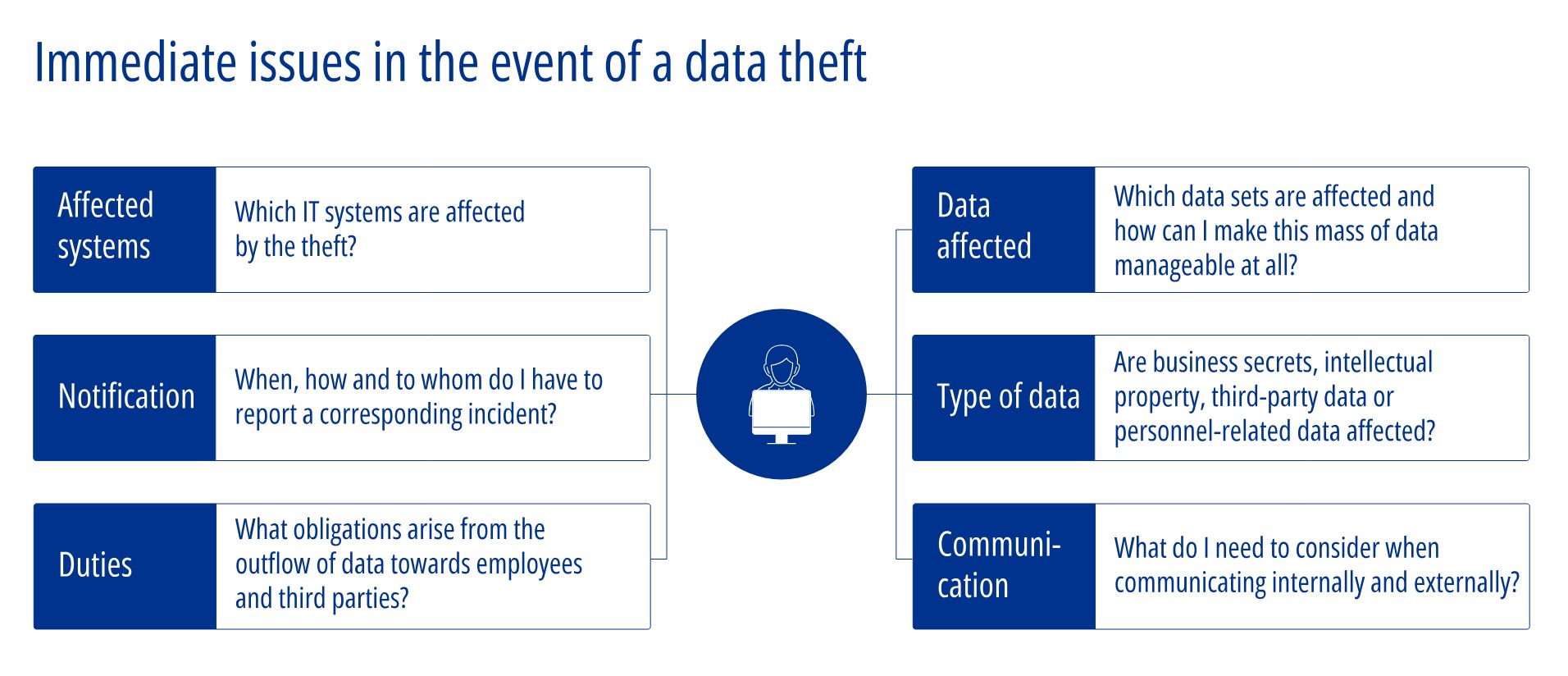
Such an incident often results in further communication and information obligations for companies, which can be associated with considerable effort and the use of human and structural resources. The sheer volume of data and lack of knowledge about its content often lead to great uncertainty and also present companies with major technical challenges. By means of tried and tested procedures and the use of current technology (e.g. machine learning), the mountains of data can be made manageable.
Based on years of practical experience, we not only support you in the clarification and complete elimination of the attack, the processing of the data leak and data content and ensure a secure restart of your business processes, but also accompany you in particular in the data protection-related processing of the incident.
During the investigation of a cyber attack, KPMG provides you with comprehensive support in:
Detection of the incident
- Containment and reconnaissance of the attack
- Identification of possible encryption of data by the attackers
- Identification of the affected IT systems
- Reduction of technical data volumes to minimize the analysis effort (e.g. DeNISTing)
Analysis of the outflowed data
- Analysis of the affected systems
- Identification of the outflowed data and files.
- Evaluation and categorization of the outflowed data with regard to:
- personal data
- intellectual property
- third party data
- trade secrets - Clarification of challenges and legal reporting obligations arising from such an incident
- Restoring ordinary procedures and operations as quickly as possible
Crisis management
- Processing of the incident
- Development of an appropriate action plan
- Ensuring adequate communication of the incident to the affected parties as quickly as possible within the legal deadlines
- Establishment of a hotline and, if necessary, other suitable internal and external communication and information channels
- Setting up and operating such communication and information channels
Your contacts
Stay up to date with what matters to you
Gain access to personalized content based on your interests by signing up today
Verena Hinze
Partnerin, Audit, Regulatory Advisory, Forensic
KPMG AG Wirtschaftsprüfungsgesellschaft
Michael Sauermann
Partner, Audit, Regulatory Advisory, Forensic
KPMG AG Wirtschaftsprüfungsgesellschaft
Connect with us
- Find office locations kpmg.findOfficeLocations
- kpmg.emailUs
- Social media @ KPMG kpmg.socialMedia

