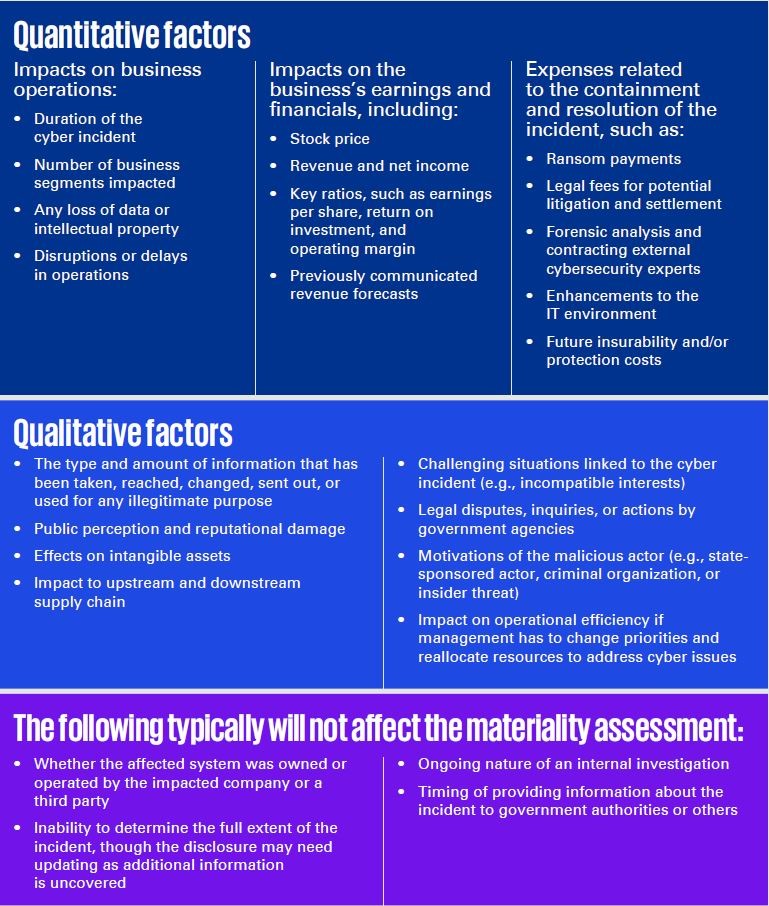
These factors are not exhaustive and may vary depending on the specific circumstances of each incident, but they provide a starting point for identifying and assessing the quantitative and qualitative impact of a breach. Importantly, these factors leave room for interpretation, necessitating further due diligence before determining materiality.
Applying new and existing materiality frameworks to cyber incident reporting
Quantitative and qualitative factors are a solid starting point for assessing materiality. However, it would be more sophisticated and prudent to leverage a combination of these factors and an established materiality framework. Most organizations already have established structures and processes for determining the severity of an operational incident. These existing frameworks, such as Enterprise Risk Management (ERM) programs, business impact assessments, Business Continuity and Disaster Recovery (BCDR) strategies, incident response strategies, and data governance and data privacy strategies, can serve as a foundation for a basic materiality framework when applied to cyber incidents.
In addition to internal frameworks, companies are starting to leverage publicly available external frameworks for assessing materiality in cyber and other accounting topics. One example is the Factor Analysis of Information Risk (FAIR) Institute Materiality Framework, based on the FAIR™ model.[5] This framework offers a detailed taxonomy of loss categories and expands the loss magnitude factor, enabling companies to quantify the impact of cyber incidents, report financial risk, and track the total cost.
Ultimately, companies should choose the framework that best suits their functions, whether it is internally developed, externally sourced, or a combination of the two. Regardless of the chosen framework, it is crucial to properly document all cyber incident materiality processes and decision points in a manner that regulators can easily interpret.
Integrating cyber response and disclosure teams
A common mistake in evaluating materiality is looking at a cyber incident solely from the perspective of the impacted company. Instead, materiality must be determined objectively and through the lens of outside stakeholders. In other words, companies must carefully determine whether an investor would consider the information related to a cyber event material to their investment decision.
In an effort to bring this multistakeholder lens to cybersecurity, many organizations are developing cross-functional disclosure committees consisting of C-suite executives, general counsel, board representatives, and finance personnel who are responsible for assessing cyber incident fact patterns and, ultimately, making the materiality determination. Integrating representatives from the existing cyber response team into the disclosure committee can facilitate a swift and comprehensive response.
The disclosure committee should be prepared to discuss various aspects of the incident and response. Consider the following questions as a starting point:
- What is the nature of the cyber incident (e.g., data breach, ransomware attack, and system compromise)?
- What is the extent of the incident’s impact on our systems, data, and operations? Did the incident impact systems related to financial reporting and internal controls over financial reporting?
- Does the incident involve sensitive or regulated data (e.g., personal information and financial data)?
- Are there regulatory obligations or compliance requirements associated with the affected data?
- What strategies have we employed to contain and rectify the incident? How are we communicating with internal and external stakeholders who may have been impacted?
- How are we calculating the financial ramifications of the incident? How are we accounting for related expenses and liabilities?
- Have we evaluated the accounting considerations around software expense capitalization, particularly if the remediation efforts result in enhancements?
- Once the incident is resolved, how should we revise our risk disclosures and financial statements accordingly?
- How are we adhering to the SEC disclosure requirements and other relevant laws and regulations? Have we assessed potential legal risks and impending lawsuits?
- Have we documented our materiality considerations at the right level of detail?
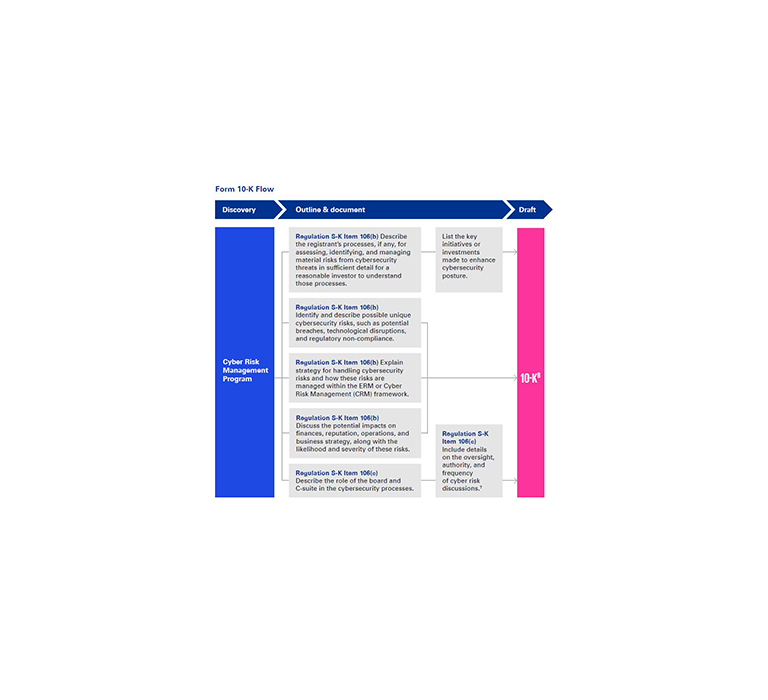
Navigating Form 8-K and Form 10-K disclosures
If a cyber incident is deemed material, then the company must disclose it on Form 8-K within four business days of making this determination.