Cybersecurity & Information Protection
- Harmonization & Reciprocity
- Meeting Minimum Standards
- Reporting Threats and Incidents
- Actions

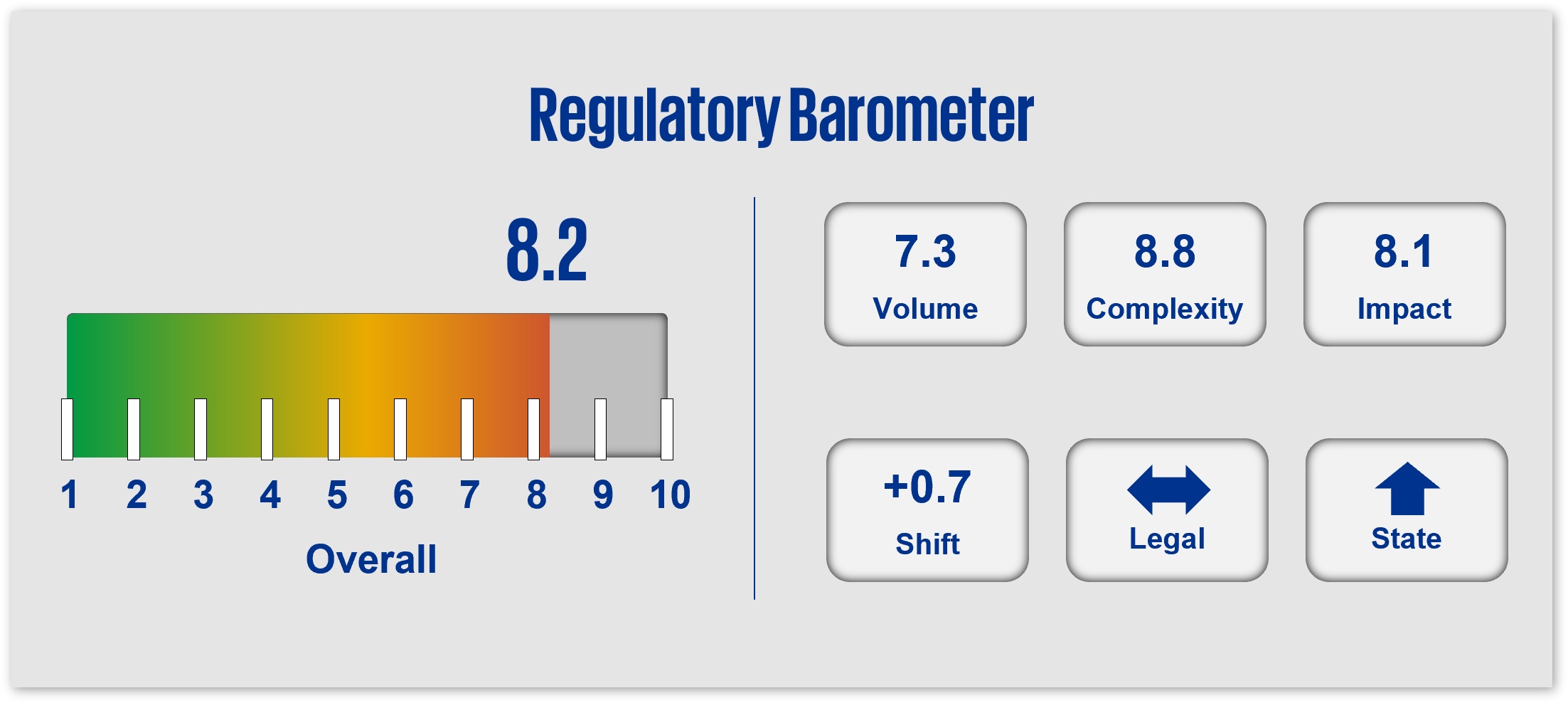
As cybersecurity risks remain a key concern across industries, and particularly relative to critical infrastructure and security, regulatory scrutiny of data security, data risk management, operational resilience, and incident response/ reporting will continue in 2025. Anticipate that federal regulatory activity will remain elevated driven by the complexities and interconnectedness of transactions, including the use of third-party AI/technology products and services and data protection/ privacy concerns. Similarly, anticipate a continuation of state adoption of cybersecurity laws and regulations.
1. Harmonization & Reciprocity
Alongside benefits of the expanding digital environment, looming threats and vulnerabilities spur calls for a unified approach to cybersecurity risk management. Under the National Cybersecurity Strategy, released in 2023 and updated in 2024, a whole-of-government effort has been underway to create a “unified cybersecurity framework” at the federal level, harmonize and streamline regulations, and establish reciprocal recognition amongst regulators and across industries.
A Cross-Sector Approach
Focusing initially on critical infrastructure sectors, initiatives in 2025 will consider:
- Setting baseline or minimum regulatory requirements across all sectors, including minimum accountability mechanisms for security and operational resilience.
- Harmonizing incident and ransom payment reporting requirements with other federal reporting regimes.
- Testing regulatory reciprocity frameworks through pilot programs.
- Supporting calls for legislation to set national cybersecurity and data privacy standards.
These efforts are separate from ongoing state-level legislative and regulatory activities related to cybersecurity and data privacy.
Supervision and Enforcement
With rising adoption of digital tools and services (e.g., cloud, e-communication technologies and platforms, fintech service providers), the volume and complexity of cyber threats (e.g., adversarial attacks, data poisoning, insider threats, and model reverse engineering) to critical infrastructure entities is increasing. In response, regulatory scrutiny is intensifying in areas of:
- Risk Management, across security-related risks (e.g., cyber/technology, operational, physical, third party) and in areas related to risk assessment, systems access, threat detection and vulnerabilities, reporting, recovery, and recordkeeping.
- Data Management, where regulators expect heightened standards related to data governance, tiering, lineage, and data quality to support enhanced reporting and risk management, as well as to cyber risk management (more targeted vulnerability and patch management) and privacy risk management (privacy rights management, privacy impact assessments).
- Cyber Resiliency, with a focus on demonstrable mechanisms to secure and fortify critical cyber infrastructure (e.g., protections against cyber incidents, technical vulnerabilities, and physical events and related business continuity planning).
2. Meeting Minimum Standards
At a minimum, regulators will continue to focus on companies’ efforts to strengthen governance and risk management around the security of systems and data both internally and through affiliates and third/nth parties.
Regulatory areas in the spotlight may include:
Compliance
With existing security-related rules and requirements, such as the SEC Cybersecurity Final Rule for Public Companies, Interagency Guidance on Third-Party Risk Management, and the FTC Safeguards Rule as well as the potential for new rulemakings and frameworks/guidance specific to cybersecurity, data privacy, or AI.
Privacy Practices
As part of an ongoing focus on data minimization, usage, deletion/disposal, controls, and consent.
Data Classification/Tiering
Given the heightened focus on data governance and management practices over risk management data, regulators will increasingly assess data classification and tiering based on data sensitivity, integrity, availability, and criticality, with due consideration for data sovereignty and localization requirements under data privacy laws.
Parties & Providers
Including companies’ abilities to demonstrate effective risk-based oversight for all types of relationships/ arrangements, giving consideration to market concentration, the interconnectedness of providers, and supply chain risks as well as assessing the provider’s ability to meet compliance obligations (e.g., incident reporting requirements) and to protect data privacy/ security.
Staffing/Resources
To ensure that cyber/data personnel possess the specialized knowledge and skills necessary to identify, analyze, and remediate emerging threats, and also that the relevant workforce is adequately staffed and resourced.
3. Reporting Threats and Incidents
Increasing cybersecurity risks and expanding expectations around threat detection and monitoring are focusing regulatory attention to reporting timeliness and adequacy both internally and externally.
Anticipate regulators will continue to review:
Board/Management Reporting
The effectiveness of board and management engagement in cybersecurity risk management and governance including:
- Roles, responsibilities, and experience.
- Oversight of processes for assessing, identifying, and managing potential cybersecurity threats and threat actors.
- Frequency, timeliness, and accuracy of reporting as well as the reporting scope (e.g., line of business, enterprise-wide, regional).
- Speed of incident remediation.
Incident Reporting/Disclosure
The timeliness and transparency of reporting disclosure for identified significant, substantial, or material cybersecurity and/or data breach incidents and ransom payments. This includes notifications, as appropriate, to:
- The primary regulator.
- Other regulatory authorities (e.g., SEC, CISA, state authorities).
- Public disclosures (e.g., Form 8K, website).
- Impacted customers.
4. Actions
- Enhance board and executive oversight: Strengthen the oversight of security risk management, strategy, and governance at the board and executive level. Conduct regular communication and reporting between executives, management, and the board to foster a proactive approach to identifying, monitoring, and mitigating potential security threats as well as timely incident response.
- Third party risk assessments: Maintain a broad inventory and perform a risk assessment of third parties involved in the delivery of business software and services to assess their operational viability, financial health, security practices, compliance history, and previous incidents. Assess potential for over dependence or over-concentration on a small number of parties/providers.
- Resiliency: Cultivate a culture of resilience, embedding robust contingency plans that encompass not just IT infrastructure but also key business operations. Conduct regular impact assessments using a variety of scenarios.
- Data Security: Build a comprehensive inventory of data (at rest and in transit) across the organization. Identify and label “crown jewel” data assets, and categorize and classify structured and unstructured data, and assess threats, vulnerabilities and risks. Align proactive monitoring and preventative data protection controls to identified data assets based on risk exposure such as Data Loss Prevention (DLP), encryption, data masking, and use of synthetic data to mitigate risk exposure to a level aligned with organizational risk tolerance and regulatory posture.
- Recovery Planning: Evaluate the ability to handle recovery at scale and under pressure; develop/ modify the backup and recovery plan as appropriate.
- Maintain transparent and timely reporting: Implement a system for transparent and timely reporting of security threat incidents, as required by regulatory authorities. All incident- related information should be accurate, up to date, and communicated to the appropriate stakeholders, including regulatory agencies and customers, as appropriate.
- Enhance Vulnerability Management Practices: Deploy advanced tools and processes for continuous vulnerability detection. Prioritize remediation efforts based on risk assessments and promptly address vulnerabilities to mitigate potential threats.
Dive into our thinking:
Get the latest from KPMG Regulatory Insights
KPMG Regulatory Insights is the thought leader hub for timely insight on risk and regulatory developments.
Explore more
Meet our team





