Phishing remains one of cyber criminals' most prolific attack methodologies, with a number of high-profile organisations from finance to media, manufacturing to engineering falling victim to the technique. Attackers use email with the aim to get users to reveal personal information such as passwords or account numbers, which later helps them break into the system or extract funds.
Unfortunately, despite growing awareness, it can be simple for an experienced cyber scammer to lure someone to click on a “dodgy” link. In doing so, they can instantly bypass a company’s firewall, undertake a full system takeover, or implement ransomware. In one swift swoop, the attack could cause untold disruption, privacy breaches, financial damage, and reputational harm.
Better security defences have been developed and implemented by organisations, but threat actors keep changing the game. The technical ingenuity and levels of social engineering undertaken by scammers have risen significantly. In some cases, even trained personnel find it hard to spot a sophisticated attack.
KPMG’s Cyber Response Services (CRS) team has seen several novel phishing attack types emerge. File obfuscation, gaining the victim’s trust, and impersonation attacks are three key tools in the scammers’ kit. Here we share some of their characteristics, as well as recommendations on how to keep your organisation protected.
Qakbot phishing - file obfuscation
In the last quarter of 2022 and into 2023, ransomware groups Royal and BlackBasta commenced phishing attacks with the malware (disruptive software) Qakbot. Qakbot has existed since 2007 but has seen significant development. Once it is loaded onto an organisation's IT system, it enables the threat actor deploying it to take control. This, along with a few other tools, allows them to launch a significant attack.
Getting malware to launch on a victim’s machine is the most difficult form of phishing to achieve. Most modern antivirus and email solutions have defences against any malicious code being run, and most people have some awareness of strange looking files. Despite this, the Royal and BlackBasta groups have had several successes.
The key to their success is replicating legitimacy and using obfuscation – which means attempting to confuse the computer as to the nature of a file. The threat group sends an email to a member of an organisation that includes a replica document from a well-known document service such as Adobe or Google Drive. The use of a ZIP encrypted file is obfuscation, as it means antivirus or email scanning solutions will be unable to see the contents.
There are some typical characteristics of these emails. These include:
- The email informs the recipient that there is a document awaiting their review.
- The document is either attached to the email or can be downloaded.
- The document is an encrypted zip file, accessible only by entering the provided password.
- An image in the body of the email provides a password to open the document, something as simple as “A123”, or “ABC5” and a “click here” button. See figure 1 for an example.
- The user is directed where to enter the password. See figure 2 for an example.
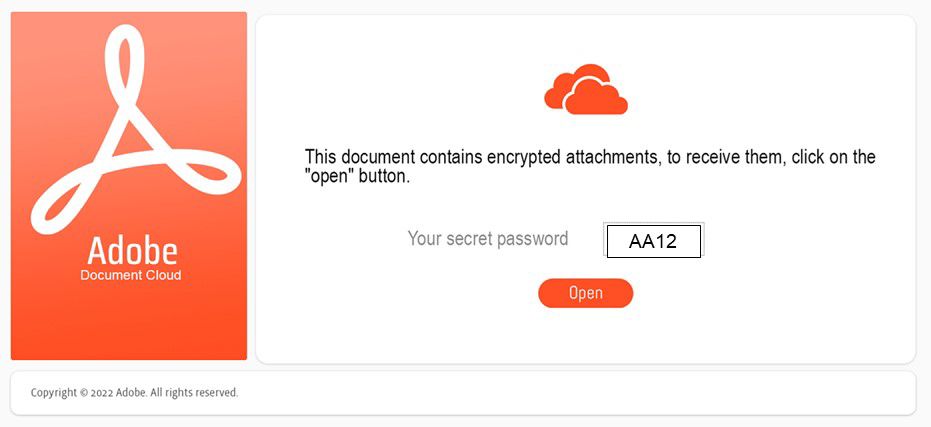
Figure 1: Contents of an email scam
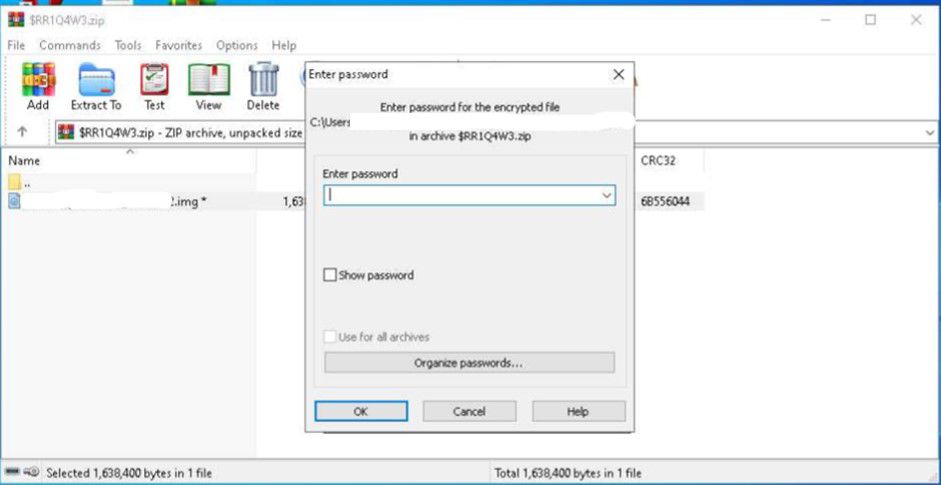
Figure 2: The user is asked to enter a password
In an alternative approach, we have observed the use of “HTML smuggling” to bypass more stringent defences. This means:
- The encrypted ZIP file is still sent with the email but is obfuscated behind encoded data within the HTML of the email itself.
- Clicking the image in the body of the email causes the browser to download the ZIP file from within the HTML code.
- When the user opens the ZIP file, they are not yet presented with their document, but with obfuscation method two, an image file with the extension “.img.”
- Double clicking on the “.img” file mounts a new storage medium to the computer, similar to plugging in a USB stick. This is a temporary storage file where the malware is launched from. These “.img” files are often set to mimic a DVD/CD ROM drive, which antivirus products may not be set to monitor in real time[MO1] [PR2] .
- If the file mounts successfully, the victim is presented with a final Explorer window. This will again contain a file purporting to be their document, however, this time the file is in fact a Windows executable that contains instructions for the computer to act on. If this is clicked, it infects the computer with Qakbot.
It may appear that this is a lot of “clicks”, and that you would not be fooled. However, careful obfuscation is not the actors' only weapon. Our next example looks at how social engineering methods gain a victim’s trust.





