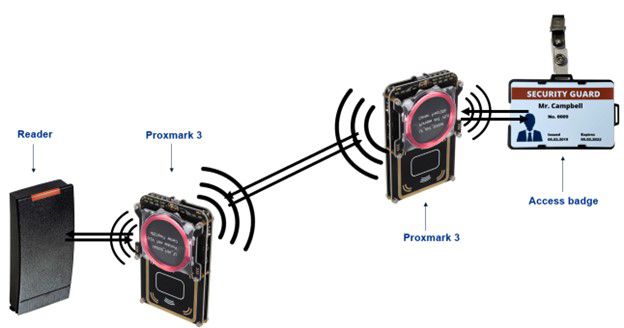
In the real world, this would mean that attackers could enter a premise with the card of an employee without ever creating a clone. This attack is also difficult to detect unless strict time-out controls are in place. In the case of supply chains, a tracker on an asset at the factory could be read directly to a reader at a distribution center of a client, making it look like the asset has already been sold and shipped.
Replay attacks
This is similar to a relay attack, except that the recorded communication from a card can be replayed to a reader. If the card is available, hackers can sniff the communication between the reader and the card using the Proxmark 3, which can then be saved and later replayed to a reader to gain access. Since this replayed communication is not real-time, cryptographic challenges from a reader cannot be answered by the card. Thus, this attack is only easily possible if the attackers know what responses to the challenges the target chip will give to the reader. This is only possible if the UID of the card is known, or the encryption is broken and Attacks on RFID protocols (iacr.org)). In the real world, this would have the same impact as cloning.
Brute forcing readers
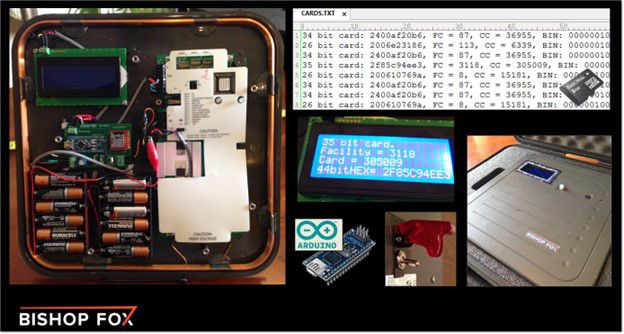
As mentioned above, each RFID card has a UID. Usually, this UID is a random number assigned by the manufacturer and cannot be changed. However, on some low frequency cards, the UIDs (Unique IDentifiers) may be sequential. Such cards are the HID Prox II and low frequency Indala cards. The high frequency cards can sometimes also be sequential such as those from NXP MiFare (see: PowerPoint Presentation (smartlockpicking.com)). When used in an RFID implementation, these types of cards allow an attacker to perform a brute force attack against a reader. This can be achieved by obtaining a known UID of the target system and moving up or down from that number one by one. This attack is usually not preferred by attackers in access control applications as there are a limited number of UIDs and since each UID is typically 4 bytes long, there are 4200 million UIDs (Security with RFID/NFC at 13.56 MHz – RFID / NFC Networking Guide (libelium.com)). In terms of the impact of this attack on access control systems, if a system grants more privileges (for example access to areas reserved for higher privileged personnel such as security guards) to higher or lower UIDs the attacker can achieve what is known as privilege escalation. In supply chain applications attackers can cause a reader to read random assets, thereby confusing the entire system about the number and location of assets. In both applications, hackers can exploit readers that are not under surveillance and infrequently used by mounting a Proxmark 3 on them to run the brute force attack for extended periods of time without interruption.
Backend attacks
These types of attacks use the memory of the RFID chip to send commands to the backend of the system (e.g., databases, middleware). Although these attacks are not common as they are very advanced, they have been proven to be feasible by researchers. Such attacks can be SQL injection (where the RFID tag sends SQL code that is executed by the database), which can delete, shut down or compromise the database. Furthermore, RFID memory can also store worms (a program that moves itself to other systems to exploit vulnerabilities) and viruses. Researchers at the Vrije Universiteit Amsterdam have found that RFID tags have the characteristics that can be used to exploit vulnerabilities in databases and middleware of RFID implementations. They provided a Proof of Concept by writing malware to an RFID tag (see: rfid_malware.dvi (vu.nl)). This can significantly impact access control and supply chain applications. For example, if the ledgers of these systems run on Structured Query Language (SQL), all the cards of employees can be deleted, making them ineligible to access the premises, or in the case of supply chains, critical databases can be disrupted.
Good security practices
Now that we have determined that many RFID cards and implementations can be (inherently) insecure, it is best to adhere to the following good security practices to mitigate these risks:
Do not use static information, such as the UID, as authentication information, but always use a cryptographic challenge-response mechanism to authenticate the card by using many different keys (such as the NXP MiFare DESFire EV1, or higher, or MiFare Plus cards). This prevents cloning of the cards, brute force attacks, and replay attacks.
Implement two-factor authentication in addition to card authentication, such as a personal identification number (PIN) or biometric authentication, to prevent all the aforementioned attacks.
Implement time-in and time-out constraints (the number of times cards or assets can be registered in the system in a specific timeframe) for cards and trackers in your system to make cloning, replaying, relaying and brute forcing more difficult.
Actively monitor security access gates with readers or limit the number of times a reader can read incorrect cards to be able to detect brute force attacks. Such attacks can be easily recognized as they show up as many incorrect cards and take a long time to complete.
Implement input validation in the backend systems to limit the risks of backend attacks through malicious injections.