Microsoft Teams has revolutionized the way organizations collaborate, enabling seamless communication and increased productivity. However, the feature that allows external users to view Teams statuses also introduces significant cybersecurity risks, particularly in the context of phishing campaigns.
The Risk of Teams Status Visibility
When external users can see the Teams status of individuals within your organization, they gain access to valuable information about user availability. This visibility is granted once an external chat is initiated. Although this feature aims to enhance communication, it inadvertently exposes critical information that can be exploited by malicious actors.
Exploiting Teams Status for Phishing Attacks
Attackers can use the visibility of Teams statuses for social engineering attacks. Here is how different status indicators can be leveraged:
- Available: Attackers might send phishing emails or links during this time, anticipating a quick response.
- Away: This status suggests the user is preoccupied, potentially lowering their guard.
- Do Not Disturb: Attackers might use this time to send emails that could be seen once the user ends the Do Not Disturb mode, potentially catching them off guard.
- Busy: Phishers might send messages that require urgent attention, exploiting the user's busy state.
- Offline: Phishers can send emails that will appear when the user comes back online, aiming to catch them off guard.
To illustrate this risk, we developed the Teams Availability Checker app. This app is currently leveraged by our in-house Red Team to facilitate specific advanced cyber-attack simulations. Because the vulnerability is still exploitable in many cases, we are currently not releasing this tool to the public.
Teams Availability Checker: A Demonstration of Risk
The Teams Availability Checker app allows users to track the availability statuses of employees. Here is how it functions:
- Tracking Statuses: Users can input email addresses and monitor whether individuals are available, away, busy, offline, or in Do Not Disturb mode.
- Status History: The app provides a historical record of statuses, showing how long someone has been in a particular status.
- Real-Time Monitoring: This feature enables attackers to send phishing emails at the most opportune times, increasing the likelihood of success.
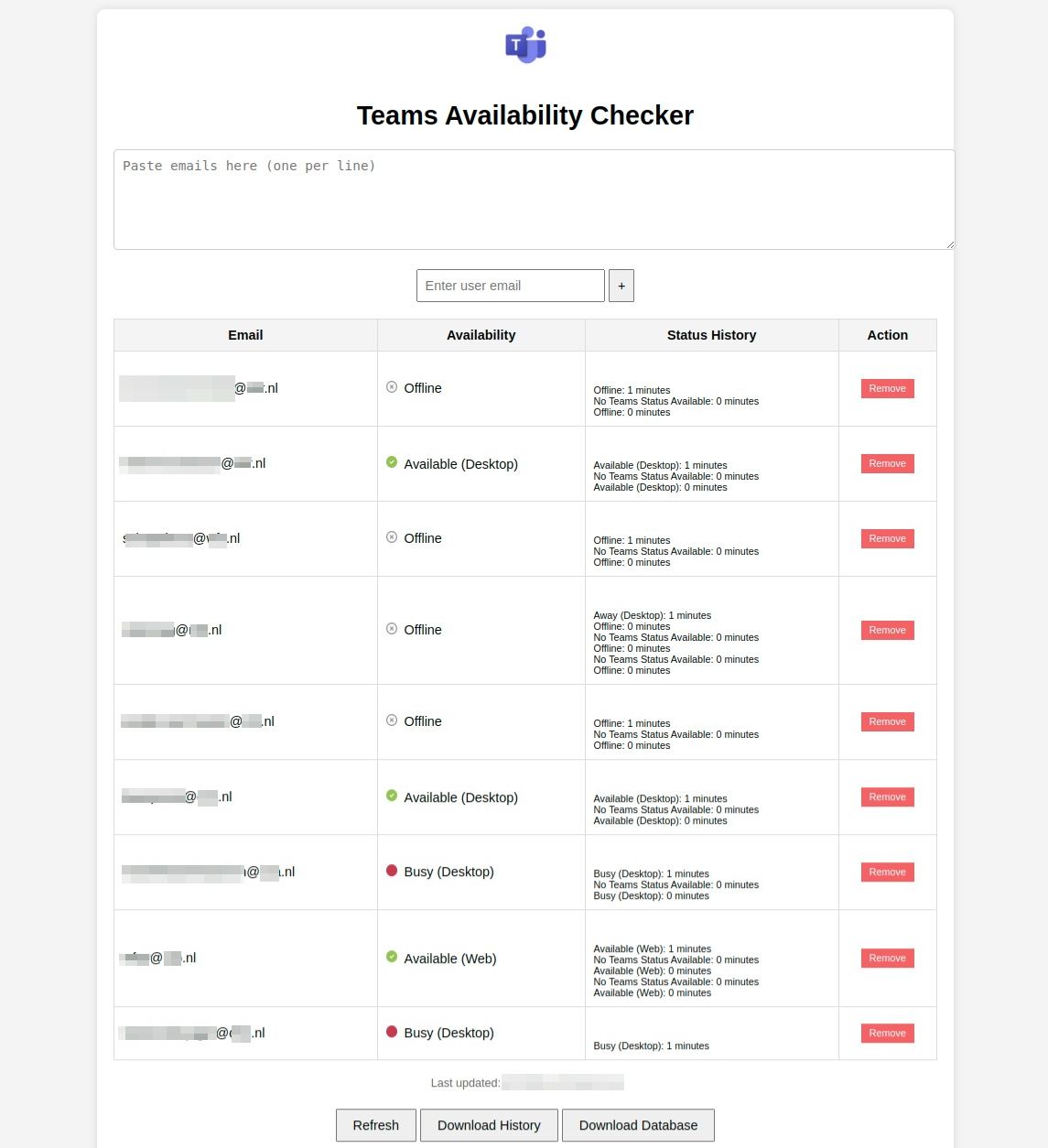
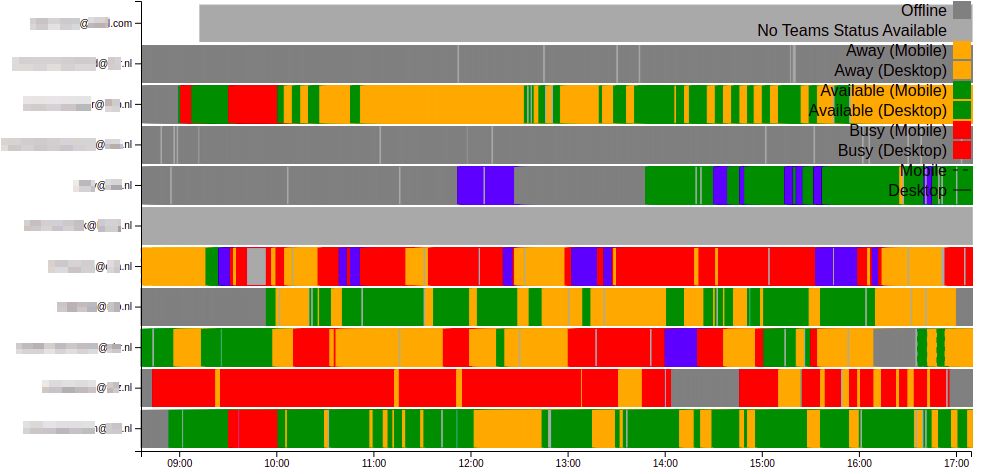
How Attackers Could Exploit the Tool
Consider this realistic attack scenario:
- Reconnaissance: An attacker inputs the email addresses of key employees into the Teams Availability Checker app. They gather data over a number days, noting when these individuals are typically online, away, busy, offline, or in Do Not Disturb mode.
- Identifying Patterns: The attacker identifies that a specific executive, Jane Doe, is usually online between 9 AM and 11 AM and then takes a break.
- Crafting Phishing Emails: A targeted phishing email is created to appear as a legitimate internal communication, such as an urgent request from the CEO.
- Timing the Attack: The phishing email is sent at 9:05 AM, when Jane Doe is online and likely to respond quickly. The email’s urgent tone is designed to prompt immediate action.
- Exploitation: Jane Doe, believing the email is from her CEO, clicks a link and enters her login credentials into a fake login page. The attacker now has access to her account, potentially leading to further attacks and data breaches.
This scenario underscores the risks posed by publicly accessible availability data. The attacker’s precise timing, based on availability data, significantly increases the chances of a successful phishing attempt.
Mitigation Strategies
To mitigate these risks, organizations should first evaluate if external chatting is genuinely necessary. Here are the key steps:
- Evaluate Necessity of External Access: Determine whether your organization truly needs to allow external users to initiate chats. Often, disabling this feature can significantly reduce security risks.
- Disable External Access: If external chatting is not essential, disable this feature in your organization's Teams settings. This will prevent external users from starting chats and seeing your Teams status.
- Educate Employees: Train employees to recognize phishing attempts and understand the risks associated with sharing their availability status. This helps in reducing successful attacks.
- Implement Privacy Mode: Enable the advanced privacy mode where only people on your Contacts list can view presence information. This reduces visibility to only trusted contacts. For more information, refer to Set-CsPrivacyConfiguration.
- Monitor External Communications: Regularly review communications from external users to quickly identify potential threats.
- Use Conditional Access Policies: Implement conditional access policies to ensure that only trusted devices and users can access Teams, adding an extra layer of security.
Additionally, Microsoft's guidelines for managing external access in Teams can provide further protection. IT admins can configure settings to control how and with whom the organization communicates externally. This includes specifying trusted domains, enabling or disabling chats with external users, and more. Details on these settings can be found in Microsoft's documentation on trusted organizations and Teams presence management.
Credits
The inspiration for this article comes from the OSINT tool developed by Dr. Nestori Syynimaa (@DrAzureAD) available at aadinternals.com/osint. This tool provides comprehensive Microsoft Entra ID tenant information for organizations, with Teams availability status being one part. The Teams Availability Checker app we developed zooms in on the Teams availability part, performing an API call to aadinternals.azurewebsites.net to fetch data.
Conclusion
The visibility of Teams statuses to external users is a double-edged sword. While it facilitates communication, it also creates potential vulnerabilities. Organizations must carefully evaluate the necessity of external chatting and take appropriate measures to protect their users from phishing attacks. Disabling external access, educating employees, and implementing privacy settings are critical steps to mitigate these risks.
Stay vigilant and ensure your organization’s Teams settings are configured to balance accessibility and security effectively. The Teams Availability Checker app highlights the importance of addressing these vulnerabilities promptly. By understanding and mitigating these risks, you can protect your organization from increasingly sophisticated phishing attacks.
This app is currently leveraged by our in-house Red Team to facilitate specific advanced cyber-attack simulations. Because the vulnerability is still exploitable in many cases, we are currently not releasing this tool to the public.

