In this blog post, we demonstrate our ability to exfiltrate data from the most secure air-gapped systems by combining state-of-the-art techniques with readily available consumer-grade electronics. Let's be clear that this exploration is undertaken within a hypothetical scenario, where we pose as nation-state backed agents, purely for the purpose of demonstrating the potential vulnerabilities.
Now, let’s imagine the following scenario: We are a special agent backed by a nation-state that is interested in a large database. This database contains the names of undercover agents operating in foreign countries and could be used to increase our intelligence operations significantly. A reliable source in the criminal world has indicated that this database is securely stored on an air-gapped system within our target organization (in this example, a governmental organization). When working in complex environments, we regularly encounter such air-gapped systems. These systems are physically isolated from the internet and other networks. Because of this disconnection, these systems have often been considered the safest systems from a connectivity perspective.
Now, let’s imagine that we have managed to infiltrate the organization. We also have physical access to the air-gapped system; however, we are concerned that the transfer of large amounts of data from this system (e.g., using a USB stick) or other media (e.g., photographs) will most certainly be detected by the Data Loss Prevention (DLP) solution. A DLP solution can be a set of technologies and policies that are used to prevent or detect sensitive data from being leaked, lost, or, as in our case, stolen. What other options are available to exfiltrate these assets?
Encoding the data into a QR GIF
As an attacker, we need to find an alternative method to transfer the database to our computer. Do we have a tool in our offensive toolkit that can transfer the database undetected? Researchers have been studying alternative methods of data exfiltration from air-gapped systems for many years. Most of the techniques are very sophisticated and high-tech, such as the following:
- Acoustic and ultrasonic techniques: Using sound to exfiltrate data.
- Electromagnetic radiation: Transfer data using electromagnetic signals.
- Infrared techniques: Transfer data between devices using invisible light signals.
- Thermal techniques: Transfer data by controlling the temperature of a computer.
- Optical techniques: Transfer data by controlling LEDs on the air-gapped system.
All of these solutions could potentially get the job done, but they’re not very practical. They would require us to bring (large) sophisticated lab equipment to perform these techniques in secure locations. A different, less complex method could be to encode the data into (multiple) QR codes. However, the file size of the important file appears to be very large. In theory, QR codes can be of any size, and there is no maximum or minimum possible QR code size. However, for our purpose, we have to take into account practicalities, such as video recording of the QR code with a consumer-grade (cell phone) camera. That’s why we want to split up the data into dozens or even hundreds of QR codes.
We are in luck, as recently an interesting tool was released that encodes the contents of a file into a GIF that plays numerous QR codes, which can be found here: https://github.com/Shell-Company/QRExfil.
The generated QR code GIF will look something like this:

Figure 1 – Example QR GIF
Hundreds of QR codes can be played sequentially. This allows us to exfiltrate a lot of data really fast.
As a thorough special agent, we created the following plan to exfiltrate the data without triggering the DLP:
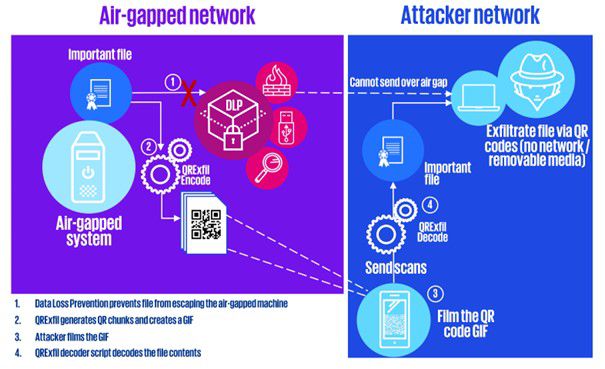
Figure 2 – The attack plan
Since we have access to the air-gapped machine, we can now run the QR encoding script on it.
<code>
./encode.sh ./secret-database.db converted-QR-secret-database.gif
</code>
Once the command is complete, we have a GIF file containing the data from your binary file. The final step is to play and record the generated GIF with our smartphone and use it at a later time when we are outside the secured area.

Figure 3 – Recording the QR GIF on the air-gapped system.
Decoding the QR GIF
Once we leave the secure facility, we can reassemble the data on our computer by sequentially interpreting the QR codes and piping the output to a file. However, the README file of the QRExfil repository mentions that the decoder script was intentionally omitted. Most likely to prevent malicious use of the scripts (by script kiddies). Of course, we were well prepared with a solution for this. As a special agent, we have only limited time (but a lot of creativity) for this mission, so we will use ChatGPT to quickly create a decoder script based on the encoder script from QRExfil.
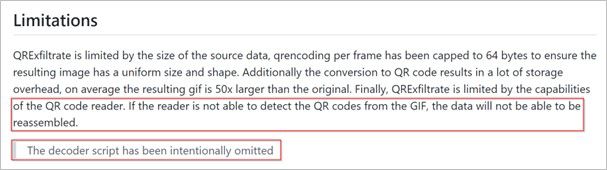
Figure 4 – Missing decoder script
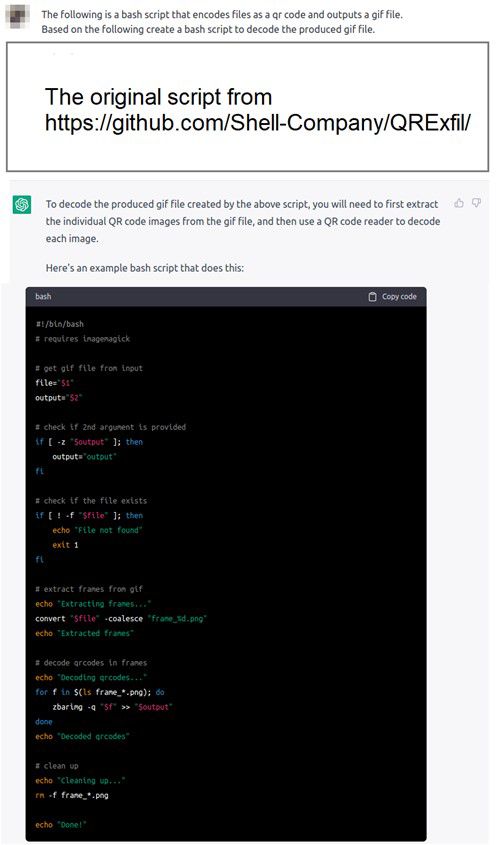
Figure 5 – ChatGPT writing the decoder function for us
The generated decoder script worked almost straight out of the first prompt. In order for the decoder script to work, we need to have 2 packages installed on our computer: imagemagick and zbar-tools.
We can install them by running:
<code>
sudo apt install -y imagemagick zbar-tools
</code>
Let’s run the decoder script on the attacker’s machine. We specify the QR GIF file as input and specify the name for the output file.
<code>
./decode.sh ./converted-QR-secret-private-database.gif ./secret-database.db
</code>
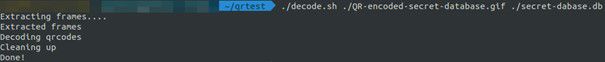
Figure 6 – The decoding script in action
Let’s read the output:
<code>
head ./secret-database.db
</code>
Figure 7 – The database is now in our possession
As you can see, we successfully captured the targeted data and can now use the information as needed.
Conclusion
This blog demonstrates an alternative technique for exfiltrating data from an air-gapped system to the machine of a threat actor.
This blog is a great reminder to focus even more on the following:
- Physical access control, to prevent unauthorized access to the air-gapped machines.
- Endpoint protection, to prevent unauthorized code execution on systems with access to sensitive data.
- Technologies that use pattern analysis of user and system behavior. This identifies anomalies or suspicious activity that may indicate data exfiltration attempts.
- Improvement of identification and detection measures to achieve Effective Security Observability. This can uncover security gaps that can have serious consequences.
- Don’t we need something on response? People and Processes?
I hope you enjoyed this blog post! If you are interested, please feel free to reach out to Frank Wiersma (wiersma.frank@kpmg.nl) for more information, comments, or suggestions. We are also happy to help you by simulating data exfiltration attacks and assessing configured defensive capabilities within your organization.
Important Notice 1: This blog is for educational purposes only. Do not use these techniques against targets without explicit permission from the system owner. This blog is part of the Blue Hat Hackers group insights.
Important Notice 2: This blog suggests the use of open-source software from public repositories. Please be aware that these projects come without a warranty and disclaiming liability for damages resulting from the use of the projects.
Discover more
Contact us
Frank Wiersma
Consultant, Cyber Assessments
KPMG in the Netherlands
We will keep you informed by email.
Enter your preferences here.



