Cybersecurity continues to be a priority topic on board agendas and remains even more critical in light of increasing geopolitical tensions, political instability, digitalization, and use of AI. As the world becomes more connected, the cyber threat landscape is expanding, and so is the critical need to ensure cybersecurity. With a shift to digital channels, collaboration platforms, and the prevalence of tools such as Copilot and ChatGPT, organizations are storing and sharing more information online and connecting more internally, as well as with both customers and third parties. This gives hackers a greater opportunity to get into your organization, navigate more broadly through it, and put it into lockdown.
The Golden Thread
Cybersecurity is a key component of ensuring stability and trust in your organization. It’s the golden thread that should run through all the organization’s decisions.
As organizations move towards the cloud, launch digital transformation programs and implement AI solutions, cybersecurity should be front and center. For example, considering a move to the cloud: who’s connecting to your environment? How are you ensuring the protection of your data and monitoring cyber threats? Similarly, how do you ensure your AI is trusted and that the algorithms are secured, so that they aren’t hacked and remain stable?
Cybersecurity is not only important for conversations about technology. It should be a key consideration in other business drivers and outcomes as well. For example, consider an acquisition: how is the potential acquiree dealing with cybersecurity? Is any of their information already available on the dark web? If so, what impact does that have on the valuation?

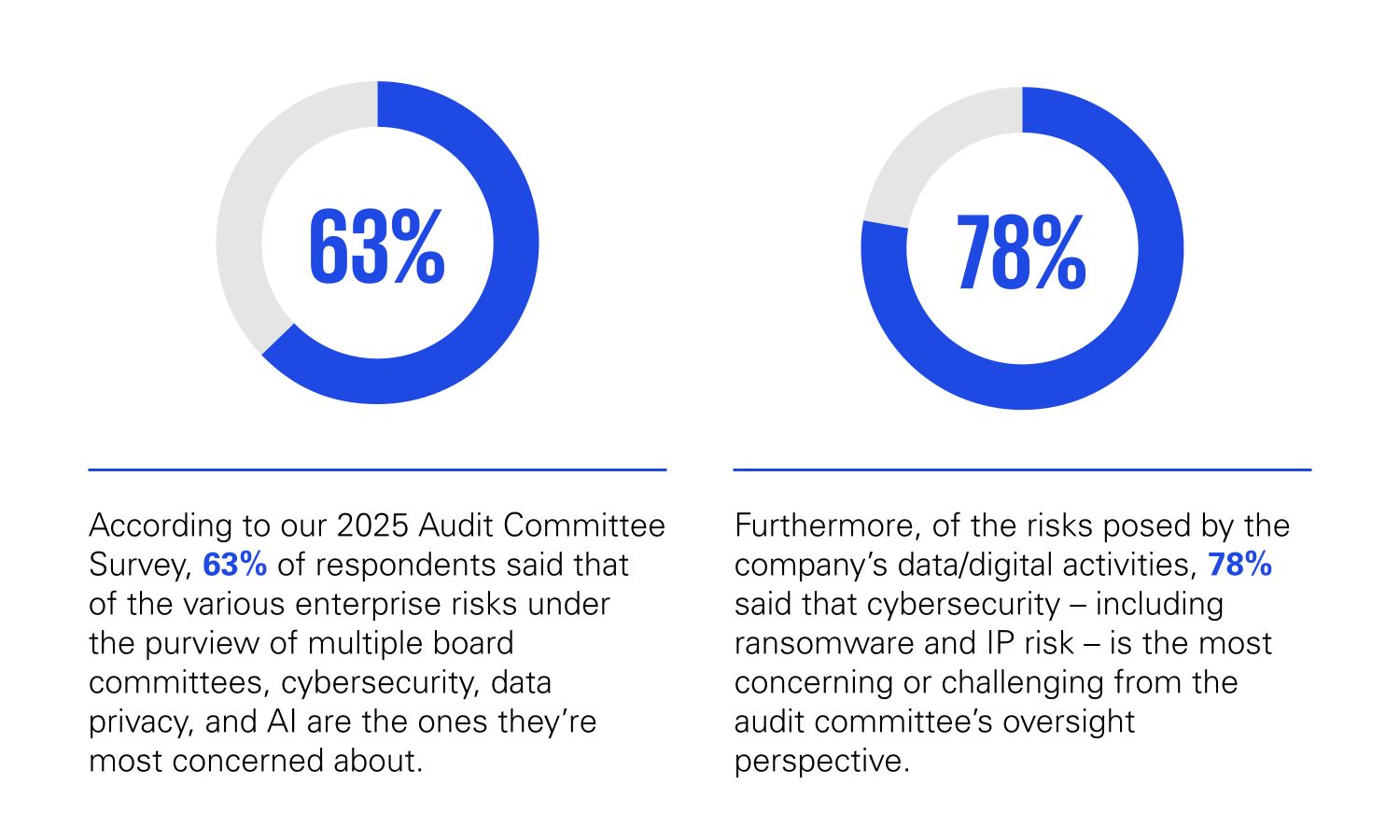
How it’s evolving
Trust – in companies, in critical infrastructures, and in the digital economy as a whole – is the new currency of cybersecurity. Once compromised, it is difficult to restore, and the consequences go far beyond technology, affecting competitiveness, reputation, and social cohesion.
Read more about the new cyber reality in our Cyber Survey Belgium 2025.

Regulatory guidelines are starting to push organizations into protecting their data and becoming more resilient to cyber-attacks. Some of the most important regulatory frameworks around cyber resilience include:
- Digital Operational Resilience Act (DORA). DORA establishes a harmonized framework for managing ICT risks in the financial sector, including banks, insurers, and service providers. It mandates strong incident reporting, digital operational continuity, and oversight of third-party ICT providers. DORA directly targets cyber resilience by ensuring financial entities can prevent, withstand, and recover from ICT disruptions
- NIS2 Directive. NIS2 expands and strengthens cybersecurity requirements across critical and important sectors, such as energy, healthcare, finance, and digital infrastructure. It introduces stricter risk management, incident notification, and governance obligations for a wider range of entities. By addressing both sector-specific and supply chain vulnerabilities, NIS2 reinforces systemic cyber resilience across the EU.
- Critical Entities Resilience (CER) Directive. The CER Directive focuses on enhancing the physical and digital resilience of critical infrastructure across 11 key sectors, including transport, energy, and banking. It requires operators to assess risks from both natural and human-made threats - including cyberattacks - and implement adequate safeguards. While broader than cyber alone, CER complements cyber resilience efforts by ensuring continuity of essential societal services.
- Cyber Resilience Act (CRA). The CRA introduces mandatory cybersecurity requirements for manufacturers and developers of connected hardware and software products. It addresses vulnerabilities at the design and development stage and imposes obligations throughout the product lifecycle, including incident handling. By targeting product-level security, the CRA strengthens the resilience of the digital ecosystem from the ground up.

- Do we have clear cybersecurity governance structures in place?
- Who is accountable for cybersecurity at the executive and board level?
- How often does the Board receive cybersecurity updates, and from whom?
- Does the Board collectively have the required technical skills or experience?
- What are our most critical cyber risks (including fragilities with the third parties) and how are they being managed?
- Do we have a current cyber risk register?
- How do we assess and prioritize cyber threats (e.g., ransomware, insider threats, supply chain risks)?
- Is our cybersecurity strategy aligned with our business objectives?
- Are we investing adequately in cybersecurity capabilities and talent?
- How do we measure the ROI of our cybersecurity investments?
- Do we have an up-to-date incident response plan?
- Have we tested our response to a cyberattack?
- How quickly can we detect, respond to, and recover from a cyber incident? Do we have scenario analysis in place?
- Are we compliant with relevant regulations (e.g., GDPR, NIS2, DORA)?
- Do we understand our legal obligations in the event of a data breach?
- How do we manage third-party and supply chain compliance?
- How do we promote a culture of cybersecurity awareness across the organization?
- Are employees regularly trained on cyber hygiene and phishing threats?
- Do we have metrics to track awareness and behavior change?
- What KPIs or KRIs are used to monitor cybersecurity performance?
- How do we benchmark our cybersecurity maturity against peers or frameworks (e.g., NIST, ISO 27001)?
- Are we tracking near misses and lessons learned?
- How are we staying ahead of emerging threats (e.g., AI-driven attacks, quantum risks)?
- Are we leveraging new technologies?
- Do we have a roadmap for continuous improvement?

Understand
Understand the key cybersecurity issues and risks. Understand the risk landscape and the response plans that exist today, the critical systems (what and where they are), the regulatory obligations that need to be met, and any relevant audit results. In their reconnaissance, attackers will be doing the same, so you need to be just as prepared (if not more).
Guide
Support management by guiding, overseeing, and agreeing to a security strategy, cyber risk management, risk appetite, accountability, and partnerships. Specifically, with regard to partnerships, remember that the way you work with third parties will have a direct impact on your cyber resilience and your reputation as a trusted organization.
Act
Take board-level actions to raise cyber awareness, challenge management, enable management (to act themselves), ensure sufficient time at board level, prepare for when an incident occurs and enable continuous enhancement.
About the Board Leadership Center
KPMG’s Board Leadership Center (BLC) offers non-executive and executive board members – and those working closely with them – a place within a community of board-level peers. Through an array of insights, perspectives and events – including topical seminars and more technical sessions – the BLC promotes continuous education around the critical issues driving board agendas.
Contact us
Explore
Connect with us
- Find office locations kpmg.findOfficeLocations
- kpmg.emailUs
- Social media @ KPMG kpmg.socialMedia