In September 2020, the European Commission released a comprehensive draft regulation on Digital Operational Resilience for the financial sector, known as DORA, as a component of a new EU Digital Finance Package.
Subsequently, on 27 December 2022, Regulation (EU) 2022/2554 and Amending Directive (EU) 2022/2556 on Digital Operational Resilience for the Financial Sector were published on the EU Official Journal and became effective on 16 January 2023.
What is DORA
The Digital Operational Resilience Act (DORA) is a new regulation (EU) 2022/2554 that aims to improve the resilience and security of the European Union's financial sector.
The regulation is designed to help protect against cyber threats, operational risks, and other potential disruptions that could harm financial stability.
How to prevent?
In the era of digitalization, intricate systems used for day-to-day operations are upheld by information and communication technology (ICT). This technology sustains crucial sectors such as finance, while also improving the performance of the domestic market. The surge in digitalization and interconnectivity has a corresponding effect on the risk of ICT, resulting in greater susceptibility of society in general, and the financial system specifically, to cyber dangers or disturbances in ICT.
To effectively respond to the ever-changing cybersecurity risks, the DORA proposal emphasizes the need to establish and maintain durable ICT systems and tools that can withstand potential threats and minimize the negative impact of ICT risks.
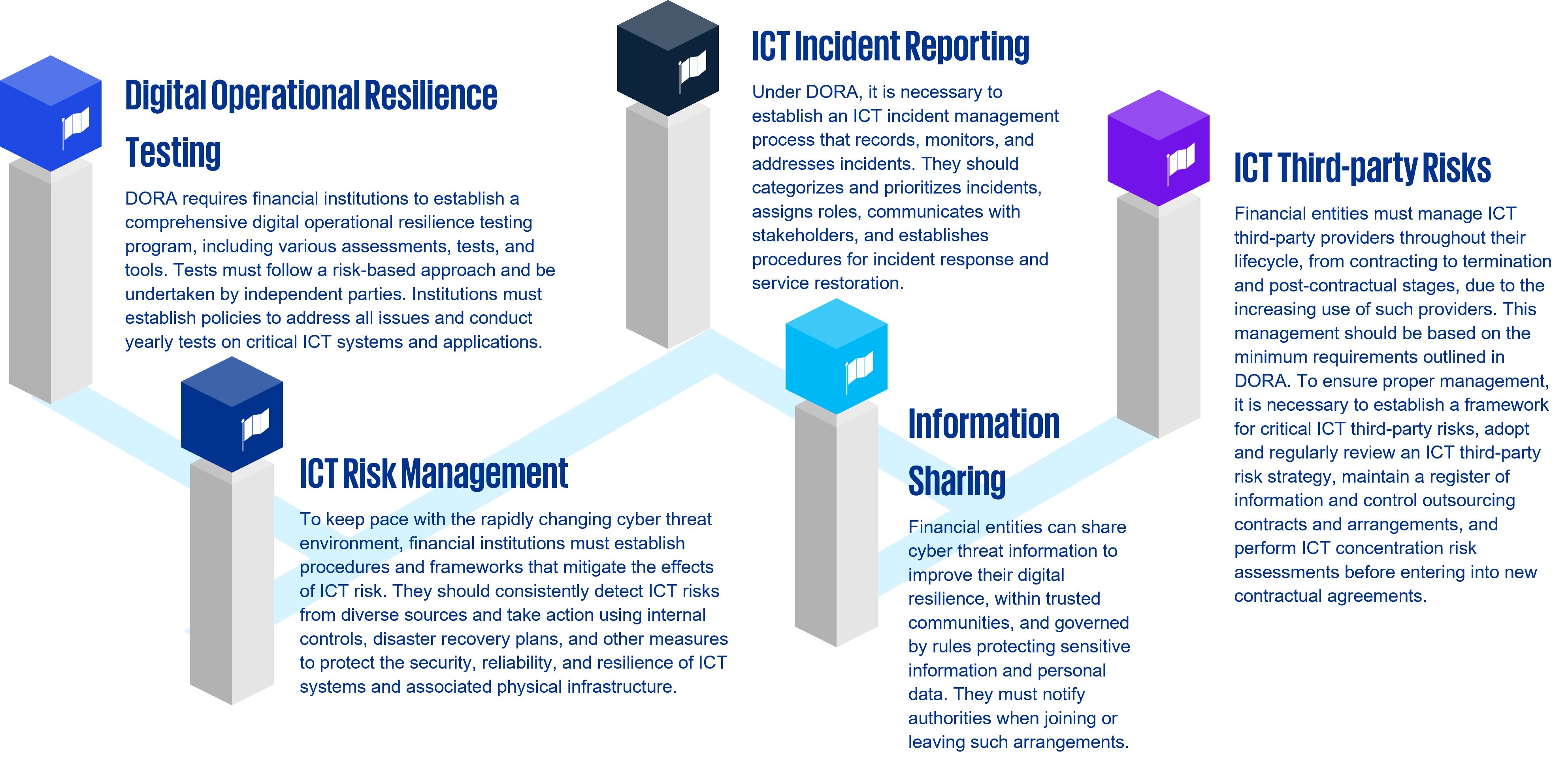
5 pillars of DORA
List of in scope entities
DORA affects various financial market participants, including banks, investment firms, insurance companies, trading venues, and more.

*including payment institutions exempted pursuant to Directive (EU) 2015/2366;
**including electronic money institutions exempted pursuant to Directive 2009/110/EC;
***as authorised under a Regulation of the European Parliament and of the Council on markets in crypto-assets, and amending Regulations (EU) No 1093/2010 and (EU) No 1095/2010 and Directives 2013/36/EU and (EU) 2019/1937 (‘the Regulation on markets in crypto-assets’) and issuers of asset-referenced tokens;
How can KPMG Cyberlab help?
To comply with the regulation, it is recommended that financial entities and ICT service providers begin acquainting themselves with the extensive list of proposed requirements.
Our services aim to safeguard your organization by providing threat-led penetration testing and other protective measures.
Check out our services here:
Red
Teaming
The Red Team concept requires a unique approach different from other security tests. It relies heavily on well-defined TTPs critical to the successful simulation of realistic threat and adversary techniques. Proper Red Team tests provide a deeper understanding of how an organization would perform against an actual threat and determine where a security operation's strengths and weaknesses exist.
Penetration
tests
Web or mobile applications, external or wireless networks, our penetration tests can help you protect your systems from attacks.
O365 cloud solution
review
We examine cloud services and filter out security issues by determining the level of risks and proposing appropriate measures.
Cloud infrastructure security assessment
Organizations are driven by cost-efficiency, flexibility, and agility to migrate to the cloud, which introduces security threats. Our service can identify security risks across all major cloud providers (Azure, AWS, Google) and their services, covering most of your cloud infrastructure.
Home office security
review
We map the remote access points of any organization from public sources to review whether an attacker can gain access to their internal network.
Vulnerability assessment
Our scans reveal publicly known vulnerabilities on servers, endpoints or network devices involved in the assessment.
Code
review
We examine the source code of applications and reveal hidden issues that could potentially compromise the security of the application, the server or the user.
Server
review
Configuration checking is a white-box type service that can complement traditional black-box testing for a more detailed review.
Security
hardening
A centralized protection service that allows potential vulnerabilities to be detected and addressed before the system is armed. 
DoS,
DDoS test
With DoS or DDoS testing we check whether a server, network or application can resist an overload attack.
Social engineering assessment
We simulate phishing attacks on the company’s email servers to test employee security awareness.
Protect your future with KPMG Cyber Lab!






