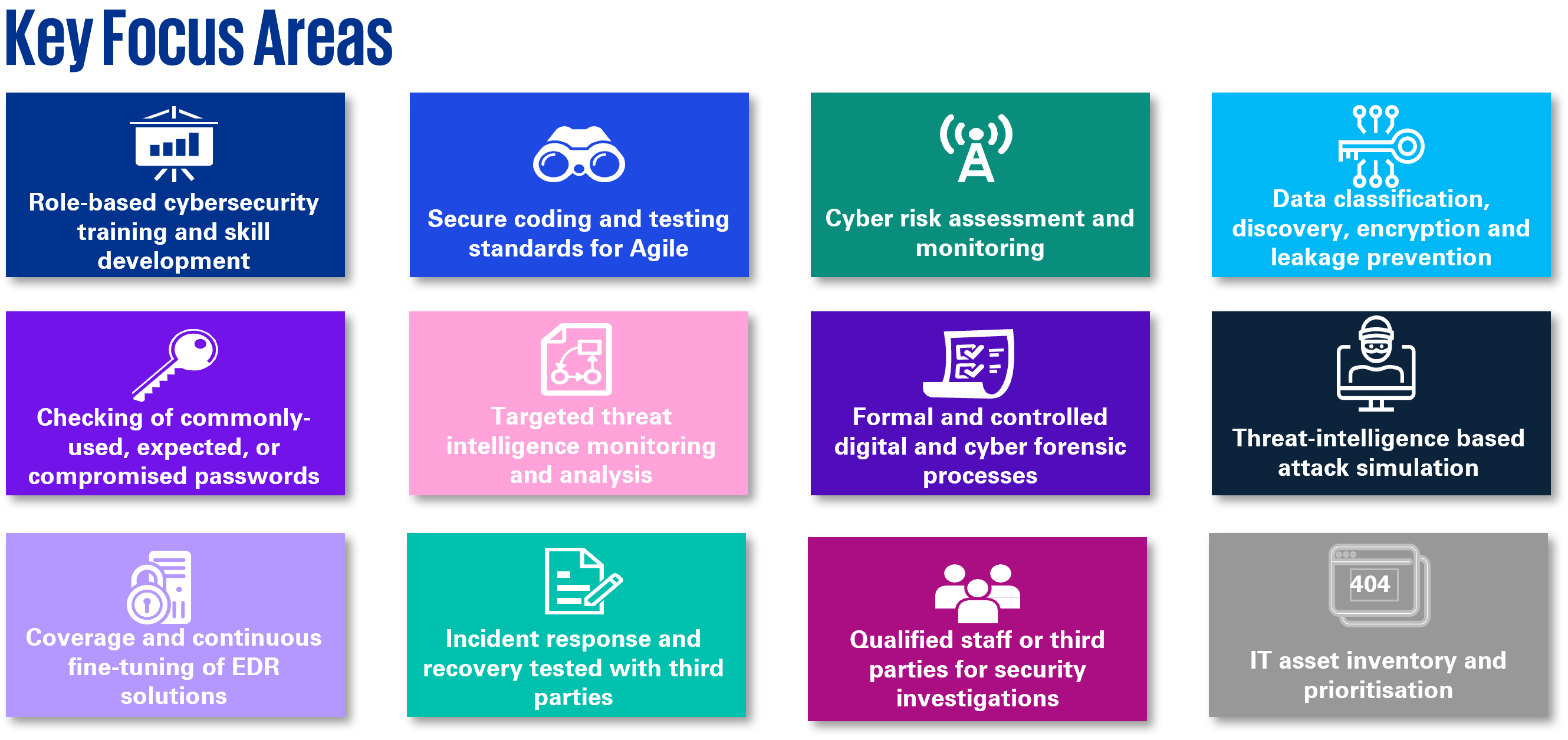
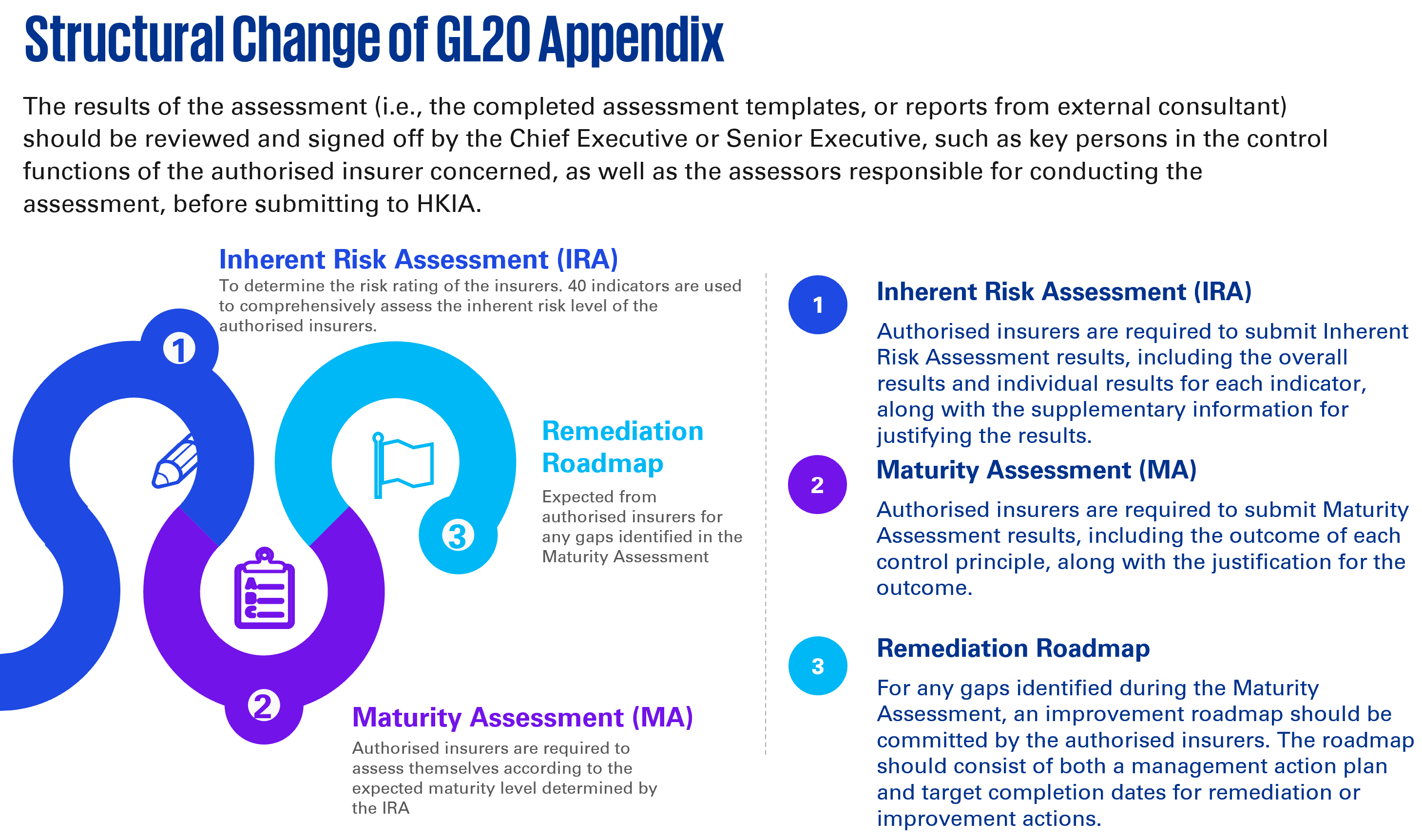
1. Some pro-active insurers have already performed gap analysis against the draft version of impending GL20 and already highlighted improvement opportunities toward the new control-based requirements. Control requirements of impending GL20 have been drafted with more descriptive statements, which some of them promote the use of more advanced security tooling and establish new control processes.
2. Threat Intelligence Based Attack Simulation (“TIBAS”) required for medium and high-risk insurer is different from the traditional penetration testing – TIBAS requires end-to-end attack simulation scenarios on top of the penetration testing of a single system or an isolated environment. It requires insurers to tailor scenarios according to threat intelligence analysis and simulate as real-life attacks in production environment conducted by competent adversaries. Insurers that do not often perform simulation exercise (such as red/purple teaming exercise) find that their IT and management team will need some more time to prepare and get ready for the test.
3. While insurers are empowered to perform their own inherent risk assessment (“IRA”), some insurers have indicated difficulties to collect necessary data and justifications due to the need to involve various stakeholders including business units for addressing criteria related to insurers’ business environment. Insurers may opt to engage with an external consultant to perform IRA in order to get an independent judgement and validate the IRA result.
4. Insurers are eager to leverage on any completed/planned assessments, audit work, and simulation exercise conducted by themselves or by other business units or group office to address the impending GL20 requirements. While HKIA has explained the suggested ways to leverage other assessments in the impending GL20 (such as scoping, assessment period, assessors’ qualifications, etc), insurers are recommended to further inquire HKIA how to operationalise in view of different scenarios and use cases.