The Powered toolkit
Our toolkit has three key elements for transformational success — a tried and tested operating model, an implementation suite and ongoing evolution services. Using them, you can turn your desired functional outcomes into reality.

1KPMG Target Operating Model
Design transformation for every level of your organisation.
You can simplify organisational goals and achieve them using KPMG leading practice, pre-configured on the platform of your choice.

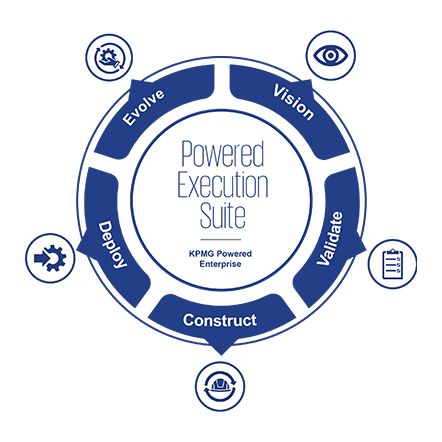
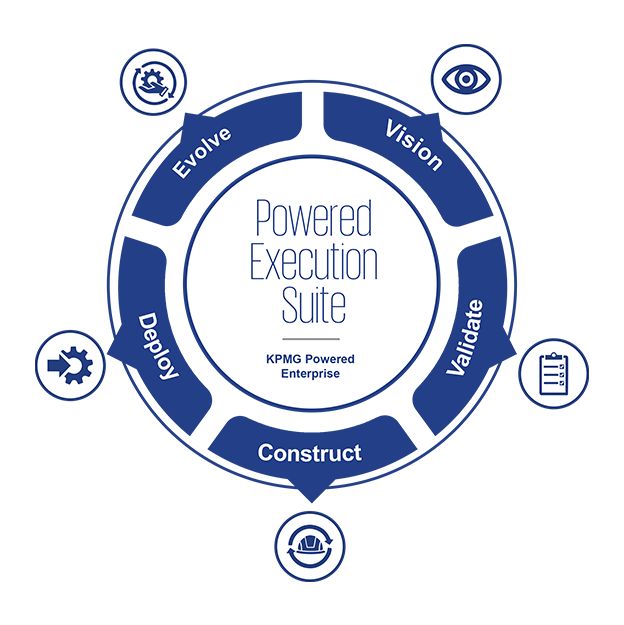
2KPMG Powered Execution Suite
Achieve transformation value faster with reduced program risk
An integrated platform with next generation tools and methods helps deliver functional transformation. It simplifies implementation and lets you unlock value faster with reduced risk.
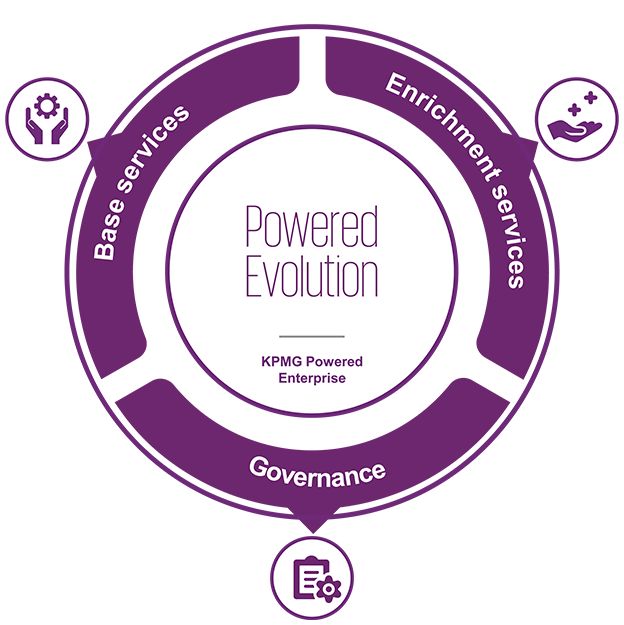
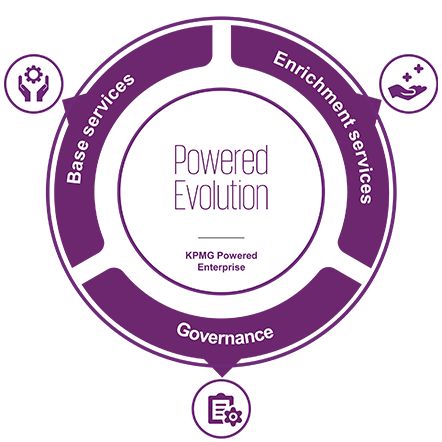
3KPMG Powered Evolution
Our specialised on-demand services make sure transformation is not a one-time exercise for your organisation, and it continually drives evolution. We let you make transformation a way of business.