The new reality has embraced the cloud. A major shift to home working driven by the pandemic is coinciding with the growing trend of outsourcing and digital transformations. The result - a heavy dependence on online solutions. Right now, the challenge of keeping your information safe is bigger than ever. It all starts with ensuring we can verify the identity of individuals and their rights to access corporate and personal information.
It isn't really new, is it? Today, working from home is thought to be integral in the 'new reality'. But in fact, we have been trending towards this new way of working for some time, as technology and internet infrastructure evolve to enable this new model. In this new reality, the risks associated with this trend of accelerated remote working, cloud adoption and use of online collaboration platforms are not new, but they are more prevalent across society. Today, practically every organization and every individual is asking the question: how do we keep our information safe?
It's not only the pandemic that has caused us to be in this situation. In order to optimize costs and to put full focus on the core objectives of the organization, we collectively outsource many business support functions. In return, a handful of suppliers require remote access to systems and infrastructure in order to keep everything running. The same applies to organizations in how they innovate and collaborate today. We are seeing more companies, institutes and governments work together to develop new solutions to problems, and to increase innovation / collaboration efficiency, these parties are being granted access to cross-organizational data, infrastructure and assets.
Employees working from remote locations are now in the center of our attention, and that’s a great opportunity! Flexibility is and will be more and more important to the modern workforce. The question is not whether it is possible to work from home (or any other place), but rather how often and when, and perhaps even for multiple employers as the gig economy develops. After all, it remains in doubt whether we will ever return to our offices in the way we used to.
It’s not just people that are working remotely though. Embracing the cloud has led to the relocation of applications and services from an on-premise data center to a virtual cloud environment. At the click of the button, you are now able to change its physical location in order to suit your business needs.
Challenges when working remotely
The office is generally viewed as a physically safe environment: closed doors, the presence of coworkers and security staff can prevent some of the incidents that could occur when you’re working from a public place. For many organizations, working remotely presents more risks and challenges than working from the office.
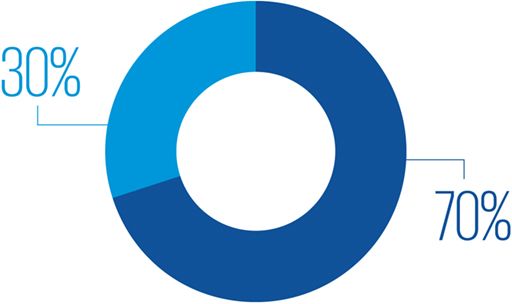
A recent study by IBM found that 70% of the organizations said remote work would increase the cost of a data breach.
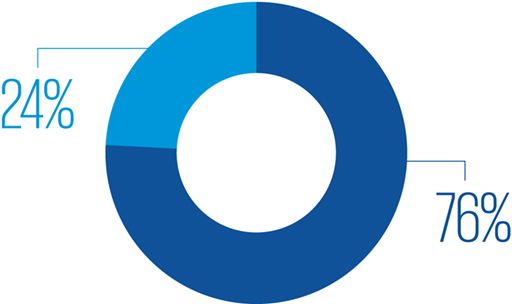
76% of the organizations indicate that remote working would increase the time to identify and contain a data breach (1).
Is it necessary to apply additional controls when we’re working remotely more often, or can we rely on the technology that we already use? Looking at current technologies such as the use of VPN and virtual desktops, you may ask yourself whether they are fit for purpose now and into the future. These technologies are mostly based on the concept of making information inside the organization available to an environment outside of the organization.
Working remotely means that anyone with an internet connection can attempt to access your information. In this scenario it is desirable to have a higher level of assurance when it comes to identity verification and data centric security, especially when it comes to verifying the identity of those attempting privileged access, access to business-critical systems or your company’s crown jewels.
How to enable your remote workforce using Identity & Access Management
Identity & Access Management (IAM) can be seen as the gatekeeper to information resources within your organization. When designed and implemented effectively, it is the answer to mitigating remote working security risks while simultaneously improving efficiency.
Consider the following areas when enabling your remote workforce:
Becoming context-aware
Context awareness is now added as a feature to IAM products in order to evaluate identities that are trying to access data based on specific variables. Variables such as the worker's location, the time of day and the device to login, are evaluated and result in a risk level. The risk level drives controls that provide additional assurance over the user’s identity. For instance, you could define that an extra authentication factor is required when someone is accessing a business-critical application or when someone is logging in from abroad or outside of business hours. The challenge we face in the new reality though is that business hours are not so black and white as they were when on-premise working was the primary way of working. The boundaries between work and home life have blurred, causing people to sometimes log in at strange times and work in very different ways.
Ensuring Identity & Access governance is up to scratch
In addition to verifying identity, it remains crucial to ensure that access rights are granted appropriately, whether working remote or locally. The quality of the overall governance (processes, procedures, approvals and monitoring) of identity and access management has a big impact on visibility and control over authentication and authorization. The more you get it right, the more likely threats will be identified before impacting your business.
Assigning responsibilities and performing reviews seems such a no brainer but a lack of these basic elements across many organizations is one of the biggest reasons why IAM-related incidents are completely missed or identified too late.
Integrating IAM with security operations
While remote working can increase the time to identify a security breach, IAM can aid in timely detection. Security incident & event management (SIEM) solutions have excellent capabilities when it comes to monitoring user activity across an organization, but it is missing the context to determine whether user activity is authorized or not. The missing context can be found in IAM. Integrating SIEM and IAM enables your SIEM solution to better identify exceptions, and IAM can be used to deactivate access in response to a threat.
Remote working is increasing rapidly, and so are the risks associated. There’s a clear need to stay on top of these risks, and IAM is a core element of the solution. Gain control over identity and access rights and ensure you and your information stays safe during the era of remote working.

