The European financial sector is in a decisive phase of digital transformation, and nowhere is this shift more apparent than in the regulatory spotlight now shining on third-party ICT providers. The recent publication on 15 July 2025 of the DORA oversight guide by the European Supervisory Authorities (ESAs) marks a significant milestone, setting out expectations, high-level frameworks, and operational details for the supervision of Critical Third-Party Providers under the Digital Operational Resilience Act (DORA). The July 2025 DORA Oversight Guide places ICT providers under direct European supervision.
The July 2025 DORA Guide on oversight activities establishes the framework for EU-level supervision of designated Critical Third-Party ICT Providers. Assurance reports — such as ISAE 3000 and SOC 2 — are key tools for demonstrating DORA readiness, building trust with financial clients and maintaining market access, not only for Critical Third-Party Providers (CTPP) but for all ICT third-party providers.
Latest DORA oversight:
Key points from the ESA guide
The new guide by the ESAs (EBA, EIOPA and ESMA) provides external stakeholders — including CTPPs, financial entities and regulators — a clearer picture of:
- Oversight architecture: Joint Examination Teams (JETs) will supervise CTPPs, leveraging harmonized, pan-European oversight and collaboration among national and European authorities.
- Scope and responsibility: Oversight complements, but does not replace, financial institutions’ own vendor risk obligations. However, CTPPs are now directly accountable to a centralized regulatory process.
- Governance practices: The guide lays out high-level governance, founding principles, and supervisory tools, emphasizing systemic risk, concentration risk and operational resilience.
- Readiness call: ESAs urge relevant ICT providers to use the guide to assess and align their operations ahead of active oversight and possible examination.
- Upcoming milestones: Most CTPPs will be notified of their formal “critical” status by the end of July, after which formal oversight — including audit, inspection, and information-access rights — begins in earnest.
Who are the Critical ICT Third-Party Providers?
Under DORA, CTPPs are ICT vendors whose services are essential to the stability and operation of the EU financial system. This group typically includes:
- Cloud and infrastructure providers
- Core software platforms and data analytics firms
- Cybersecurity and networking companies
- Critical data providers
CTPP status is assigned using criteria such as scale of service, degree of substitutability and concentration risk in the European financial market.
What does this mean for local or other ICT providers?
While only a select group of providers will receive the formal “critical” designation and be subject to direct oversight by the European Supervisory Authorities (ESAs), financial institutions rely on a much larger ecosystem of ICT third parties. Many ICT vendors may not meet the pan-European criticality threshold but still support core, high-impact operations for banks, insurers, and other regulated entities in a particular country or sector. These local or other vendors will still face rising demands from financial institutions for stronger controls and independent assurance. In this new landscape, assurance reports such as SOC 2 and ISAE 3000 can be a decisive factor in winning and retaining clients. For many smaller vendors, this is also an opportunity: a clear assurance posture can differentiate them from competitors and position them as trusted partners for regulated institutions.
Why assurance matters for all ICT third parties
Assurance refers to an independent evaluation process whereby qualified auditors assess a provider’s controls, processes, and practices across areas such as information security, business continuity, risk management and regulatory compliance. This evaluation is formalized in assurance or attestation reports that give objective evidence of the provider’s ability to manage risks, safeguard data and uphold operational resilience.
Assurance reports typically include:
- Assessment of control design and effectiveness (e.g., security, availability, confidentiality)
- Testing of incident management and business continuity frameworks
- Verification of data privacy and regulatory compliance procedures
- Insights on risk governance and continuous improvement practices
Assurance is becoming fundamental for all ICT third parties, for the following reasons:
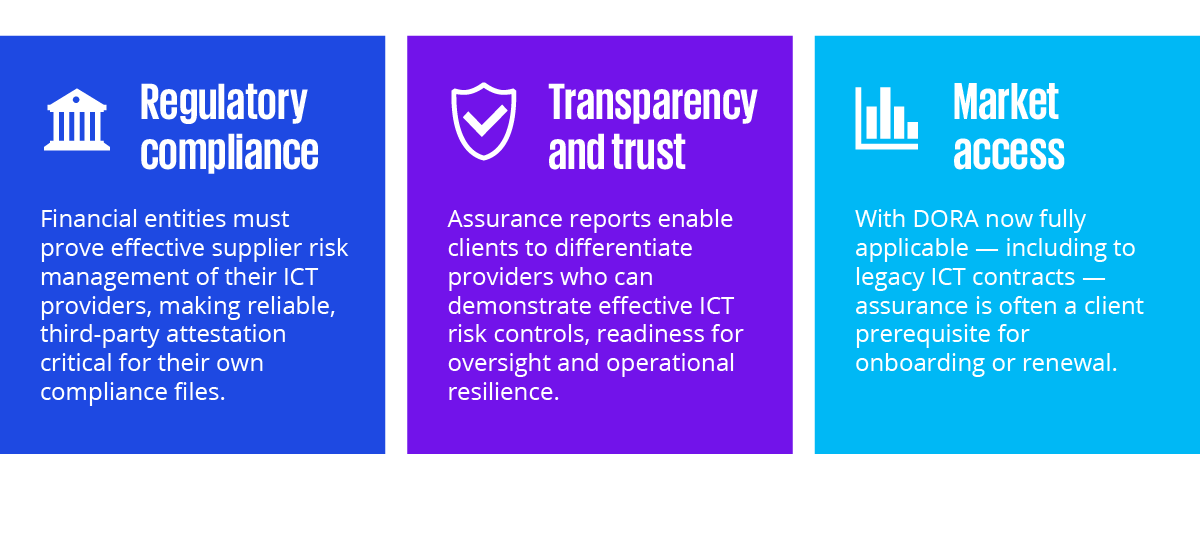
A robust assurance posture isn’t just about clients — it’s a business asset:

How can assurance be provided?
International standards provide the backbone of trust:
- ISAE 3000 / ISAE 3402: International frameworks for attesting to non-financial and financial controls.
- SOC 1 / SOC 2 / SOC 3: Key US frameworks, highly relevant for attesting to information security, availability, confidentiality and processing integrity.
For CTPPs or other ICT third-party providers serving regulated financial entities, SOC 2+ and ISAE 3000 are especially pertinent, as they can directly align with DORA’s requirements for operational resilience, data security and incident response.
ISO/IEC 27001 vs. assurance reports
A common question among ICT providers is whether an ISO 27001 certification alone is sufficient from an assurance perspective.
(ISO/IEC 27001 is the international standard for information security management systems, focusing on establishing, implementing, maintaining and continually improving security controls.)
It’s important to distinguish between ISO/IEC 27001 certification and attestation (assurance) reports:
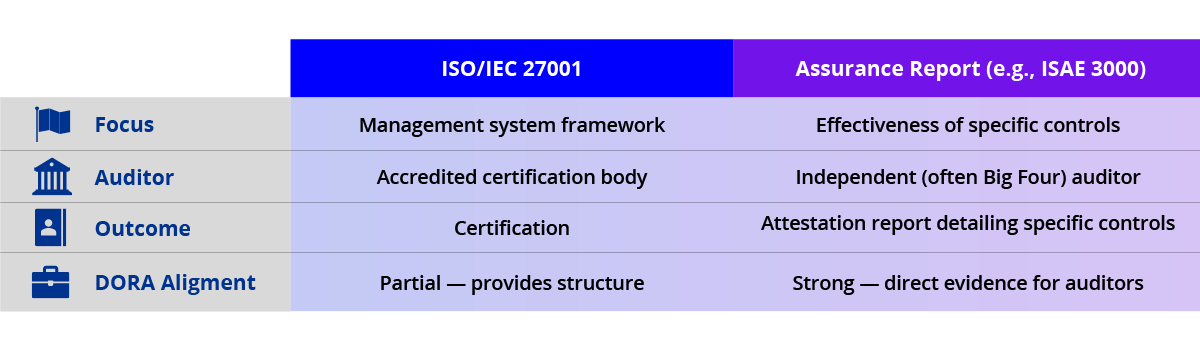
While ISO certification offers a solid baseline, we believe that internationally recognized assurance reports provide greater value to clients and stakeholders seeking to understand the design and effectiveness of their service providers’ controls and to map these controls to their own risk frameworks.
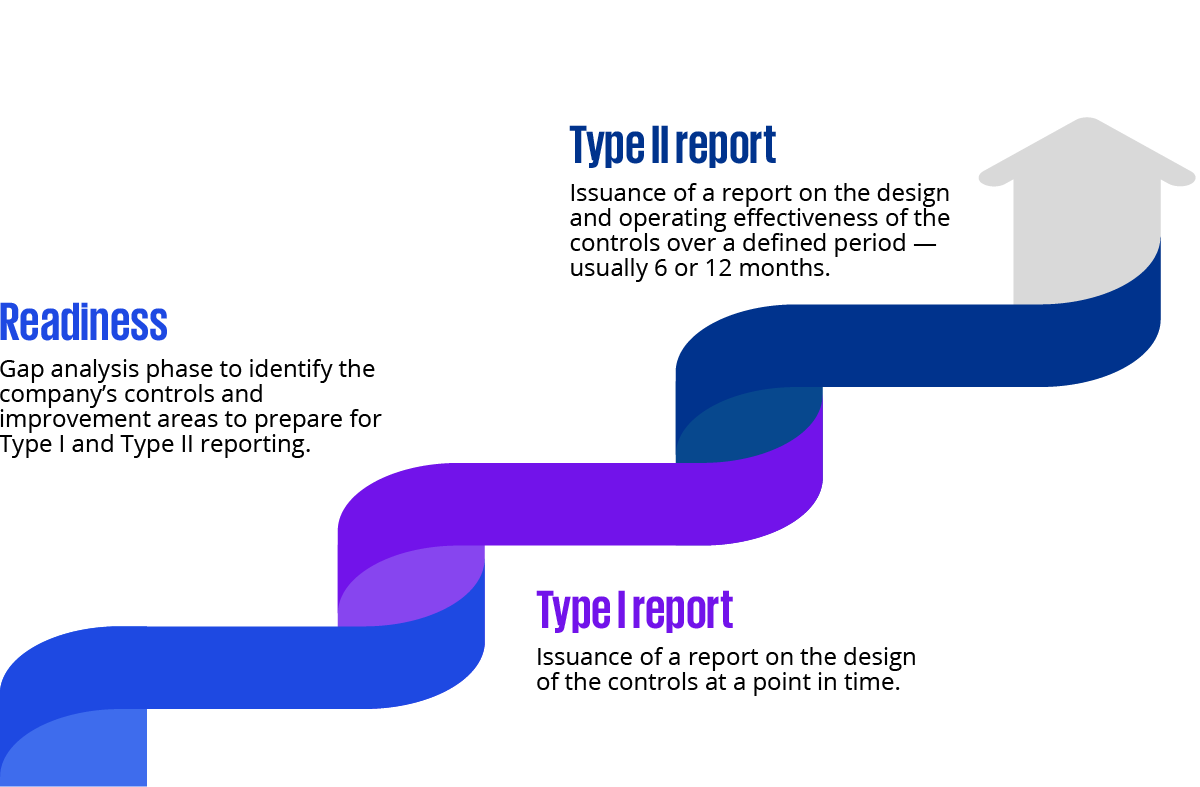
How to prepare: Readiness, Type I and Type II approaches
A typical assurance journey entails:
- Readiness assessment: An internal/external gap analysis to identify what controls you have and what’s missing relative to SOC 2 or ISAE 3000 and DORA obligations.
- Type I report: Attests to control design “at a point in time.” Useful as a first step and for initial compliance signals.
- Type II report: Attests to the operating effectiveness of controls over several months, which is most relevant for regulatory and client trust.
Already have a SOC report? Integrate DORA
If you are already running SOC or ISAE audits, leverage this by expanding your scope to include DORA’s new requirements:
- Update control maps to cross-reference DORA mandates (e.g., ICT third-party risk, incident management, penetration testing).
- Collaborate with auditors to ensure their attestation explicitly supports DORA compliance.
- Provide your latest reports proactively to clients and keep them ready for ESA oversight requests.
KPMG view
The July 2025 ESA oversight publication signals a new era: attestation and assurance reports are not merely “good to have” but are becoming essential for trust, compliance and market access.
By embedding recognized assurance frameworks into your operations and aligning them with DORA, ICT service providers can not only meet regulatory demands but secure a competitive edge — demonstrating resilience, accountability, and a proactive stance in Europe’s fast-evolving digital finance landscape. Organizations can accelerate their DORA readiness with expert guidance from KPMG, ensuring robust assurance frameworks and a competitive edge
KPMG expertise and our accelerators
Leveraging extensive experience in regulatory compliance, cybersecurity and third-party risk, KPMG guides organizations through the complex demands of DORA and ESA oversight. Our teams combine regulatory insight with hands-on technical know-how to help clients assess, design and implement end-to-end control environments aligned with the latest European requirements.
KPMG’s proprietary accelerators streamline every step of the DORA assurance journey, including:
- Accelerated readiness assessments: Rapid diagnostics leveraging benchmarked control catalogs mapped directly to DORA and SOC 2/ISAE 3000 frameworks.
- Control implementation playbooks: Step-by-step guides for embedding robust ICT risk, incident response, and business continuity controls in line with regulatory expectations.
- Audit and attestation automation: Toolkits for evidence gathering, documentation and reporting — making assurance renewals faster and more reliable.
- DORA-SOC/ISAE mapping matrices: Pre-built crosswalks ensuring that existing assurance programs comprehensively address new DORA requirements, reducing duplication and accelerating compliance.
With a multidisciplinary approach spanning regulatory, technical and operational domains, KPMG stands ready to support your organization — not just in meeting compliance, but in building a competitive, resilient and trusted ICT partner profile in Europe’s evolving digital landscape.




